Businesses in today’s globally connected world rely on digital infrastructure. Determining reliable security measures is essential because of this. As the world migrates to cloud computing, SaaS applications attention must be paid to cloud security. The protection of sensitive information and upholding operational integrity depend on it. So let’s get started by going through this post and learning more about cloud security. The benefits, issues with privacy and security, and factors affecting businesses will all be covered.
💡Over 100 zettabytes of data will be kept in the cloud by 2025. [ 1 ZB = 1 billion TB = 3 Trillion GB ]
What is Cloud Security?
Gartner defines it as “the processes, mechanisms, and services used to control the security, compliance, and other usage risks of cloud computing”. It entails putting security measures in place to protect against unwanted access. Data breaches and other online dangers are also thwarted. To guarantee the privacy, accuracy, and accessibility of data and services, cloud security employs many levels of defense. Supports a variety of technical controls, rules, and processes. 45% of breaches occur in cloud environments. That’s a high number. Especially for defenseless organizations that haven’t yet secured themselves.
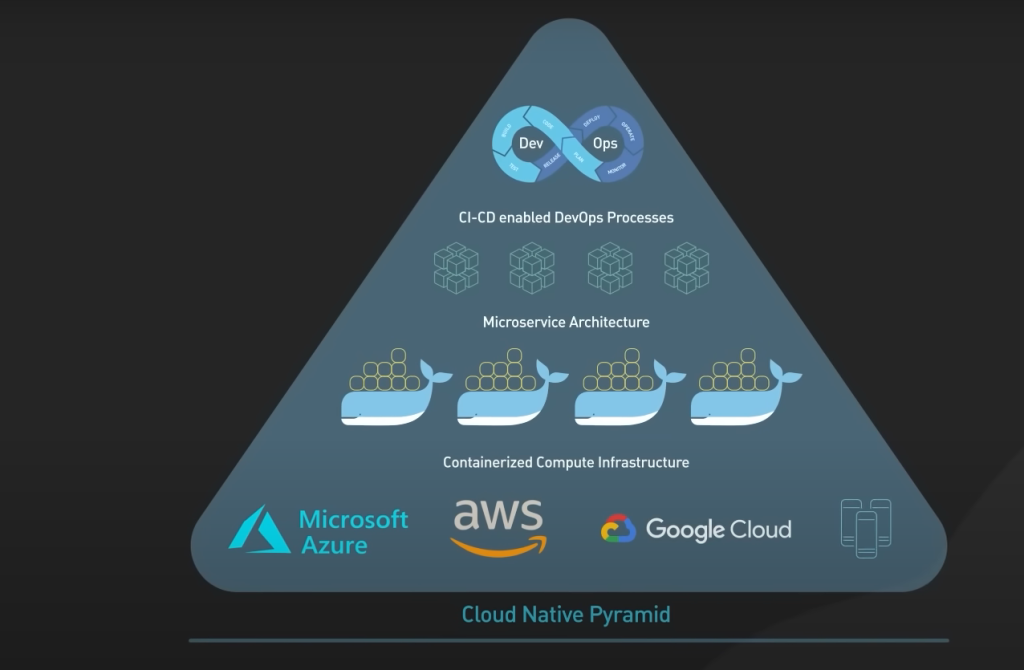
To understand cloud security, you must first understand the cloud computing and deployment architecture
Cloud Security Options
Three key categories of cloud security options:
- Public Cloud. Used by many orgs and administered by an outside entity. The external organization is in charge of the system’s security as well as other elements like maintenance and general upkeep.
- Private Cloud. The only utility is for internal computing within a single firm; not for external transactions or collaboration. Even if it costs more, it offers better personalization and security.
- Hybrid Cloud. This solution combines both private and public systems. Also comes with encryption and quick scaling. Although it could be a little expensive, it is the most effective for all types of work that businesses need to do.
💡 The market had a total value of $371.4 billion in 2020. The market is anticipated to reach $832.1 billion by 2025 with a compound annual growth rate (CAGR) of 17.5 percent.
The Big 3 Public Cloud Service Providers
In 2023, the top three cloud service providers are:
- 62% of the market is occupied by AWS (Amazon Web Services)
- 20% goes to Microsoft Azure
- 12% goes to GCP(Google Cloud Platform)
Oracle Cloud and IBM Cloud are worth consulting too. Also, several fresh “specialty suppliers” are offering competitive services.
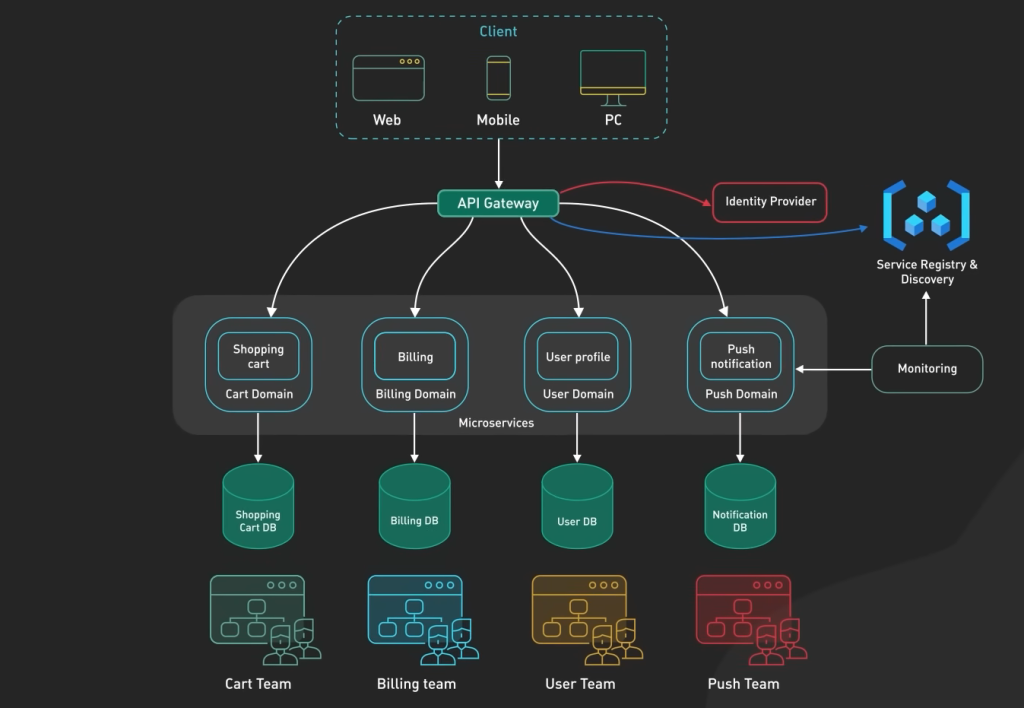
Key Components of Cloud Security
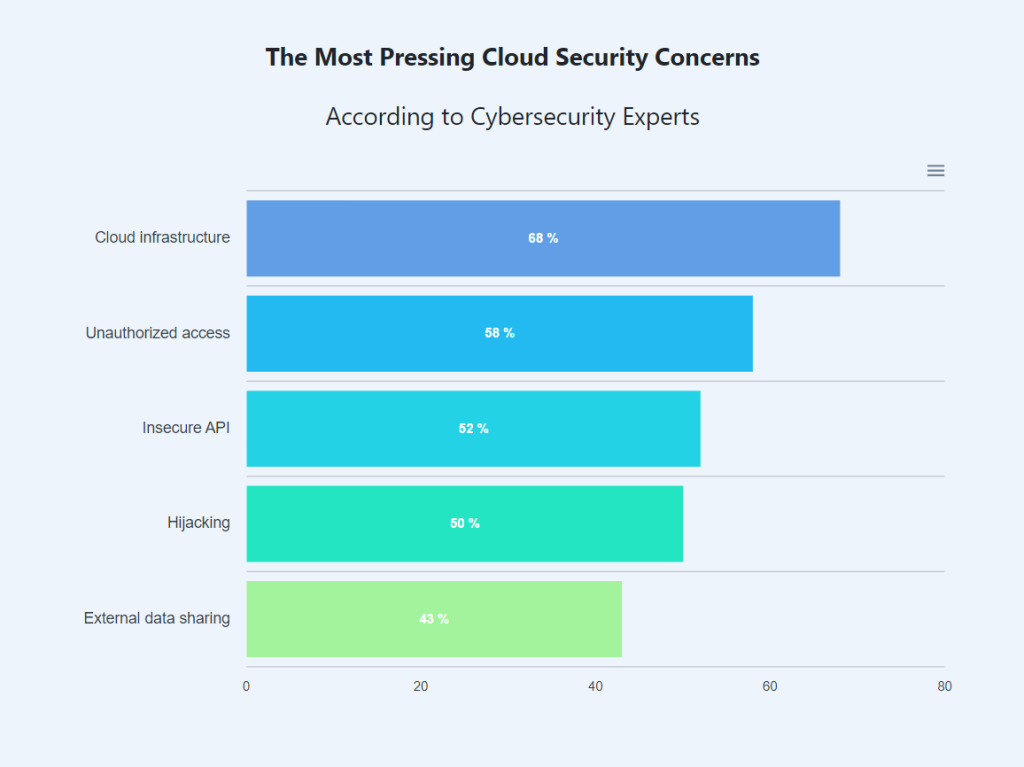
⚠️ 96% of organizations reported significant difficulties when putting their cloud strategy into practice. This is because of high management complexity and engineering hours. Wouldn’t it be great if a CNAPP solution provides abstraction and guarantees all this? An ideal solution will take care of all items listed below.
Vulnerability Control
The goal is to identify and fix potential flaws in cloud systems. To prioritize vulnerabilities for remediation, regular vulnerability assessments and scans are helpful. The risk of exploitation is reduced by patch management. It makes sure systems stay updated with the most recent security fixes. Stay ahead of new threats with ongoing monitoring and threat intelligence.
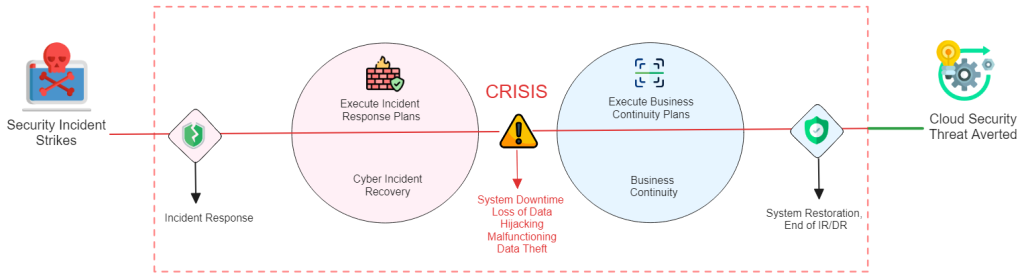
Incident Response and Disaster Recovery
Be prepared to handle security incidents because no security system is completely fault-proof. The steps to take in the event of a breach are having response plans, reducing the impact, and promoting a quick recovery. Data backups and replication are two disaster recovery strategies. Both guarantee business continuity and the ability to resume operations in the event of a major incident.
Access Controls and Authentication
The cornerstone of cloud security is authentication. It confirms users’ and devices’ identities before allowing access to resources. Prevent unauthorized access with robust authentication techniques like MFA. Access controls decide the rights and privileges of authenticated users. Only people with the proper authorization can access particular information and services.
Encryption of Data
Protects sensitive data in the cloud. Data is encoded in a way that can only be unlocked with the right encryption key. Ciphering during transmission and at rest makes it non-decipherable to unauthorized parties. Even in the event of interception or compromise. To guarantee the confidentiality and integrity of data, manage keys and choose strong encryption algorithms.
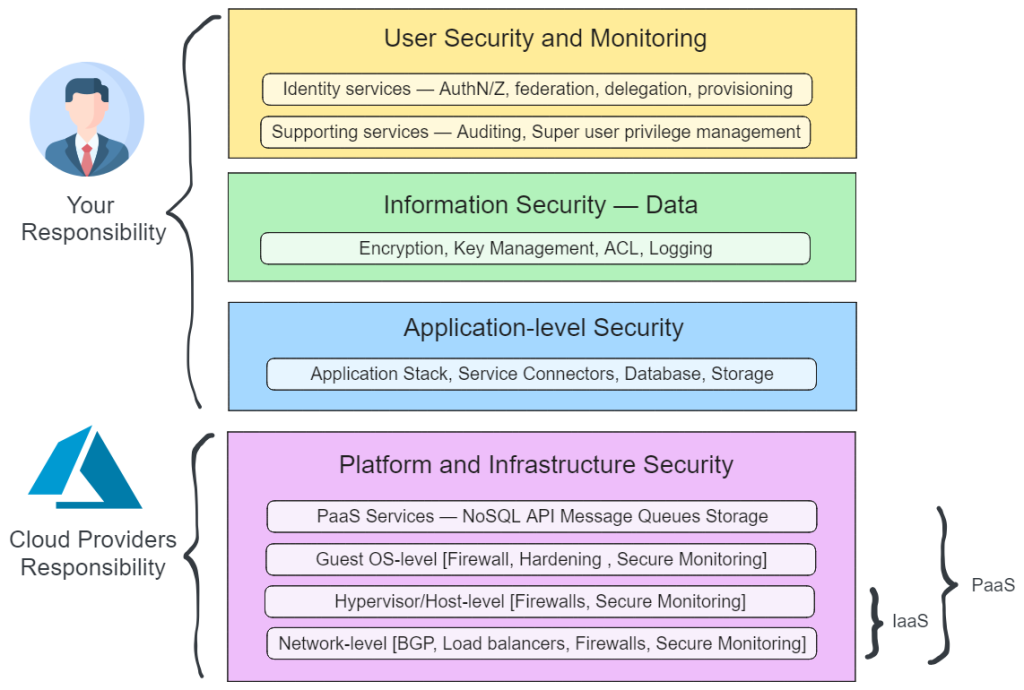
Benefits of Cloud Security for Businesses
Cloud security is of paramount importance for businesses. Offers valuable advantages that significantly impact operations and success. Some cloud security benefits businesses are:
Enhanced Privacy and Data Protection
To guarantee the confidentiality and protection of sensitive data, cloud security measures use cutting-edge encryption technologies and access controls. To reduce the risk of data breaches enterprises need strong authentication mechanisms. Eg. MFA, Authenticator, Secrets Management. Customers have more trust as a result. Businesses reduce costs to abide by data protection laws.
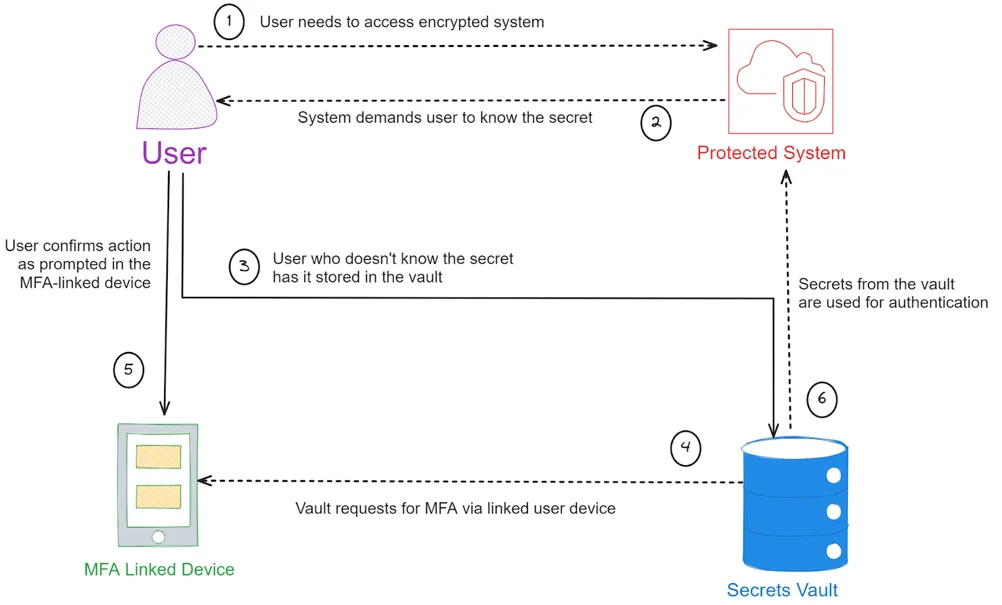
Improved Compliance and Regulatory Adherence
For companies in every sector, adherence to regulatory requirements and data protection laws is fundamental. Cloud security solutions aid with regular security audits and obtaining the necessary certifications. Data processing and storage practices must adhere to the necessary standards. Achieve this by choosing a compliant provider (HIPAA or GDPR). This also prevents undue fines and reputational damage.
Scalability and Flexibility
Because of the inherent flexibility and scalability of cloud security, organizations change their security protocols in response to changing demands. Cloud security solutions are more flexible than conventional on-premises security infrastructure. They adapt to changes in the business environment. Security measures scale in accordance with security needs. Whether you are experiencing rapid growth or need more security. Advanced threat intelligence and ML-driven cloud security identify and address emerging threats.
Cost Savings and Operational Efficiency
Cloud security offers cost savings and improved operational effectiveness. It reduces on-site infrastructure, maintenance expenses, and security personnel. Cloud service providers handle system maintenance, software patches, and hardware upgrades. Industries can scale security measures according to their budget and needs. The pay-as-you-go cloud security model eliminates significant upfront investments.
10 Key Indicators to Evaluate Cloud Service Provider Security
With cloud computing, the network nodes grow exponentially. With the pros of cloud computing comes the high attack risk surface due to so many devices. Every choice matters. Modern times require enterprises to gear up and ensure proper safety compliance.
There are plenty of cloud security service providers on the market. Before making a decision, assess security capabilities. In all the clamor, it’s simple to get lost. To decide based on a company’s needs, take into account the following factors.
Evaluation Checklist
Adherence to Security Standards and Frameworks
- Does the service provider abide by industry standards like ISO-27001, ISO-27002, and ISO-27017?
- What about relevant governmental and regulatory standards such as GDPR, CCPA, HIPAA, and PCI DSS?
Audit Operational and Business Processes
- Is there proof of their adherence to corporate, governmental, and industry standards?
- Is access to security events, log data, and third-party security reports provided through their SLA?
Strong Authentication and Identity Controls
- Do they have robust authentication and identity control infrastructure to mitigate access risks?
Vendor Governance and Access Policies
- Do you have access to internal management tools, corporate audit trails, and transparent security service pricing?
Data Storage and Confidentiality
- Where is data stored? Geographical location determines data laws.
- Is the required level of security and confidentiality up to the expected standard?
Integration with Third-Party Security Solutions
- Support integration with third-party security solutions for added control and customization?
Uptime and Performance
- Data durability and 99.99999% (rule of 5 nines) availability. Uptime and performance metrics.
- What are their track record outages and average resolution time?
History of Data Breaches and Losses
- Has the provider experienced any data breaches or losses in the past?
- What were the underlying reasons, and who was at fault?
Backup and Disaster Recovery
- Is robust backup and disaster recovery processes in place?
Exit Strategies
- Options for exit strategies in case security, costs, performance, or business strategy changes?
- Are you avoiding lock-in situations that may result in prohibitive costs for leaving?
To succeed in the long run, consider prospective cloud service providers based on their security protocols and how well they fit your company’s needs and goals.
| Cloud Security Practices | Usage in the US | Usage in Europe |
| Security Automation | 38% | 38% |
| Container Firewall | 38% | 38% |
| Cloud Vendor Security Policies | 36% | 36% |
| Security Policy Automation | 34% | 34% |
| CSPM (Cloud Security Posture Management) | 42% | 26% |
| CWPP (Cloud Workload Protection Platform) | 42% | 26% |
| CNAPP (Cloud Native Application Protection Platform) | 42% | 26% |
| Observability or Security Tools | 33% | 24% |
| PSP (Policy Security Policy) or PSA (Policy Security Automation) | 31% | 22% |
| Kubernetes Network Policies | 32% | 15% |
| Free CVE or Paid Scanner | 26% | 18% |
Cloud Security: Safeguarding Digital Assets
The increasing popularity of cloud computing equals increasing threat levels and attack surfaces. A variety of techniques and tools are applied to safeguard data, applications, and infrastructure in the cloud environment. Let’s examine the various facets of cloud security and highlight the best practices that most businesses require.
Ensuring Cloud Network Security
Network Segmentation and Isolation
Segmenting the network into separate parts reduces the potential impact of a security breach. Each segment focuses on particular access controls, which prevent threats from moving within the network. Isolating sensitive information and crucial systems eliminates all baseline risks.
Intrusion Detection and Prevention Systems
IDPS tracks network packets, spotting and neutralizing potential threats. It recognizes suspicious activity, like malware or unauthorized access attempts, and acts to stop further harm. Strong IDPS solutions improve the confidentiality and integrity of cloud-based networks.
Secure Network Configuration and Monitoring
Prevention is preferable to treatment. This proverb most accurately describes cloud security. Safeguarding network communications involves putting in place stringent access controls, powerful firewalls, and secure protocols. Continuous logging and monitoring also reveal unusual activity or potential security breaches. Avoid security breaches at all costs. Maintaining cloud security requires a secure network configuration.
Protecting Cloud Data
Secret Vault and Encryption
Data at rest and in transit is made unreadable and unusable even in the event of unauthorized access by encrypting it. Additionally, effective key management practices, including secure key storage and rotation, maintain the confidentiality and integrity of encrypted data.
Data Recovery and Backup
To reduce the risk of data loss and ease quick recovery in the event of an incident, must install regular data backup and recovery processes. Customer information, leads, internal documents, passwords, and user accounts can all be lost if not handled. Cloud service providers have automated backup solutions. They ease data redundancy and facilitate disaster recovery without delay. Replicas sold worldwide are also popular. When a zone of availability is down, servers retrieve data from another location.
Data Loss Prevention Strategies
Data classification, content inspection, and policy enforcement are three DLP strategies that work to stop the unauthorized transmission or leakage of sensitive data. These controls help organizations stay in compliance with data privacy laws and safeguard the integrity of their priceless data. They add an extra layer of security to cloud data protection.
Top cloud challenges for today’s organizations
💡 The most crucial cloud initiative, according to European organizations, is shifting more workloads to the cloud (70 percent). Optimizing current cloud usage to reduce costs comes next (59 percent), and then advancing a cloud-first strategy (50 percent).
| Challenges | Percentage |
| Security | 85% |
| Lack of resource/expertise | 83% |
| Managing cloud spend | 81% |
| Governance | 77% |
| Managing software licenses | 76% |
| Compliance | 76% |
| Central cloud team/business unit responsibility balancing | 73% |
| Cloud migration | 73% |
| Managing multi-cloud | 71% |
Secure Cloud Servers
⚠️ Human error, not cloud providers, is the cause of cloud breaches in 88 percent of cases. Men are twice as likely as women to fall for phishing scams, with a fall rate of 34%.
Updated systems and Path Administration
Patch management and regular system updates reduce vulnerabilities and defend against known threats. To address potential security holes and lower the risk of exploitation by malicious actors, robust processes are crucial.
Hardening and Secure Configuration
Minimize the attack surface and make infrastructure robust. Adhere to industry standards.
- Apply access controls
- Remove default accounts
- Adopt least-privilege principles and hardening controls
- Implement secure configurations
- Disable unnecessary services are all part of secure cloud servers.
- Never install untrusted third-party extensions and packages.
Logging and Ongoing surveillance
Constant monitoring and log management identify and address security threats. These mechanisms:
- Track user activity
- Spot potential security holes
- Simplify forensic analysis
- Offer insights into the readiness of cloud infrastructure for preventive risk management.
Best Practices for Cloud Security
Maintaining cloud security adds value to organizations. MFA, enforced complexity, and frequent updates enhance it by motivating users. It’s good to stick to the best authentication practices.
Security Evaluations and Audits
Checks the effectiveness of the security controls highlighting any vulnerabilities and gaps. Allowing businesses to address weaknesses to better equip the infrastructure plane.
Programs for Education and Awareness
Employee vigilance, security awareness, and proactivity in cloud computing, data handling, and security-related practices foster a group defense against potential threats.
CIA Triad
C – Confidentiality, I – Integrity, A – Authorization
Cloud security is a complex discipline that requires careful consideration and implementation. Always keep the CIA triad in mind while adopting security solutions.
Zero Trust is the ideal framework for cloud workloads. It is the singular most effective approach that will be dominating the industry.
Key Takeaways
🎯 Focus on Cloud Security. Businesses suffer severe repercussions if they continue to be hesitant about cloud security solutions. Data theft or an intrusive cyberattack are also the last things any small business wants. Data loss due to cyberattacks is actually more common than you think.
🎯 Proactive Risk Management. Adopt a Cloud Security Posture Management (CSPM) solution. This will identify and resolve misconfigurations, ensuring compliance with industry standards.
🎯 Intrusion Detection and Prevention. Track network traffic and block malicious activities.
🎯 Data Privacy in the Cloud. Encryption protocols enhance data privacy and protect sensitive information from unauthorized access.
🎯 Access Controls and Identity Management. Use the least privilege access controls and identity management practices. Adopt Zero Trust based access to cloud resources.
🎯 Regular Security Audits. Helps to identify vulnerabilities, ensure compliance, and maintain a strong security posture.
🎯 Employee Training and Awareness. Educate your team about cloud security best practices. Campaign about password management, phishing awareness, and cautious data handling.
🎯 Continual Monitoring and Incident Response. Make several incident response plans to detect and respond to security incidents.
Conclusion
“Despite the advantages, cloud computing comes with an added vulnerability if data is stored incorrectly or if the provider’s own security is compromised,” says Gartner practice leader Matthew Shinkman.
“To mitigate these risks, executives will need to guarantee that their cloud security strategy keeps up with the pace of this growth. Recent regulatory changes, such as GDPR, and growing scrutiny at the board level about cybersecurity mean the risks associated with what has become a standard business practice are on the rise.”
This report highlights the Top 10 Most Damaging Breaches in Cloud Security. You obviously do not want this for your company.
As a business, your goal is to:
- Provide value to users
- Scale quickly
- Defend against cloud threats
- Comply with regulations and legal requirements
This is where CNAPP solutions come in, providing a singular solution to all business needs and problems. This article discussed the three-tiered approach for data, network, and server security. Dashboard monitoring is also very much needed as you’ll need to monitor and keep an eye out for anomalies.
As an up-and-coming business, expect to be targeted. This paranoid approach is complemented by the Zero Trust Architecture – “trust nothing, verify everything.”
There is no better time than right now to shift to cloud computing and cloud security solutions. Ad-hoc practices lead to significant losses down the line. Understand that data loss and cyberattacks may affect even the largest enterprises. In hindsight, cloud security will need to be a top concern if firms wish to spur long-term success.
We advise a cost-effective cloud backup solution to deal with data loss, common cyberattack threats, and dangerous hackers. Nascent corporations have had a difficult time making the switch from traditional internal system management and data storage to contemporary cloud computing.
FAQs
What are the common security risks associated with cloud computing?
Data breaches, unauthorized access, and service disruptions. Least-privilege principle, monitoring, and good secret management methods guarantee safety.
Can cloud security be customized to suit specific business requirements?
Absolutely! Cloud security can be tailored to fit your business needs and is customizable. Whether it’s implementing access controls, encryption protocols, or specific compliance requirements.
How does cloud security enhance data privacy compared to on-premises solutions?
With robust encryption, strict access controls, and continuous monitoring. Use a secure vault for your data, that remains rotates keys periodically, uses MFA, and thwarts man-in-the-middle attacks.
What role does encryption play in securing cloud data?
It protects sensitive data by scrambling it into an unreadable format. It is only accessible to authorized users acting as a secret code. Boosts data security and protection against potential threats. Popular in communication channels.
How often should a business perform security audits on its cloud infrastructure?
Regular security audits maintain a secure cloud infrastructure by identifying vulnerabilities, ensuring compliance, and maintaining compliance. Experts recommend biweekly scans for large enterprises and fortnightly scans for medium to small-scale organizations.