Gartner defines CNAPP as “a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production.”
CNAPP can be approached from two perspectives: DevSecOps or standard IT security approaches. The former implies a greater emphasis on securing the apps themselves, while the latter prioritizes expanding traditional network-level safeguards. This blog will provide you with in-depth insights on industry leaders as well as emerging solutions that offer new solutions.
The Need for CNAPPs
Organizations must overcome integration hurdles in cloud-native application security (CNAPP). This makes tracking risks, finding weak spots, and patching vulnerabilities easier. According to VMware’s State of Observability survey, an average cloud app usage is up to 50 distinct technologies by 57% of respondents.
Several cloud service providers are being used in a multi-cloud fashion. This has become the new norm to diversify risk and go beyond using the leading PaaS providers (AWS, Google, and Azure). It blends private, public, and hybrid cloud computing solutions, using serverless computing, and virtual machine instances. Also, higher adoption rates for Kubernetes containers and microservices have been recorded.
Businesses need to control risks, identify weak points, and eliminate vulnerabilities to cope with application hazards. Sysdig’s cloud-native security report states that 73% of cloud accounts have exposed Amazon S3 buckets. CNAPPs are adopting intelligent automation to reduce misconfiguration errors. Professionals who detect coding errors in cloud configuration improve development process security. CNAPPs are complementary tools to this process.
According to Palo Alto Networks’ State of Cloud Native Security 2022 survey, 80% of companies using open-source security technologies have insufficient or weak security postures. The proportion of firms hosting more than half of their workloads in the cloud has doubled since 2020. This rise is handled in the serverless world.
Containers are the building blocks of cloud-native apps. Corporate clients have pieced together tens or hundreds of different security products with little to no automation, protection must be quick and undetectable. Cloud security’s success is linked to the fact that clouds have become the de facto computing layer for enterprises.
60% of organizations transfer workloads weekly between on-premises and off-premises. The maturing of the CWPP business is driven by the growing prevalence of cloud workloads and Linux servers.
A Note on Balancing Features and Budget
What cloud artifacts can you find and scan regularly? Certain products (Lacework) do not expand far beyond the top three IaaS providers. Others (Tigera) only support the main three Kubernetes services. Others (AccuKnox) delve deeper into containers and the many Linux servers that power them. The actual question is, Can you track all these artifacts in near real-time?
Can you blend agents and agentless in the main dashboard, reports, and policies of the product? How do events get reported? Are there separate access rules in place so that different personnel can focus on different aspects of the picture? Is it possible to collect agent and agentless data using distinct or combined pre-built security policies? How useful are your dashboards and visualizations for displaying the current situation of your cloud security?
Is each of the four management tools covered? Some suppliers, like AccuKnox for Cloud, include CWPP and CSPM components, but you will need to install extra components to secure Kubernetes and non-Azure clouds. Tigera takes a different approach, focusing on container-based infrastructure.
For managing cloud deployments, infrastructure-as-code frameworks such as AWS Cloudformation, Terraform, Demisto Azure Blueprints, etc. Unfortunately, few vendors are open about their pricing. The most complicated is the Data Theorem, which includes calculations for API usage, web and mobile apps, and cloud resources. Tigera is slightly better but still complicated. CheckPoint and AccuKnox provide reasonable rates, while AccuKnox is the most straightforward, charging $2,500 for 100 units, with unit prices of $25 per month. Some providers generate fictitious units or package pieces that hide details.
| Company | Integration Approach | Free Trial | Pricing |
| CheckPoint CloudGuard | Offers integration with both CWPP and CSPM solutions | Provides a free trial period | From $625/ month for 25 units |
| CrowdStrike Falcon Cloud Security | Supports integration with both CWPP and CSPM platforms | Offers a free trial option | $300/year for a basic plan |
| Prisma Cloud | Provides integration capabilities for both CWPP and CSPM approaches | Offers a free trial opportunity | $9,000/year for every 100 Business Edition credits |
| AccuKnox | Supports both agent and agentless integration approaches | Offers a free trial option | Starter Kit from a monthly rate of $2,500 for 100 units, with unit prices of $25 per month |
| Wiz | Specializes in CWPP integration using an agentless approach | Offers a free demo, but no specific free trial mentioned | Pricing details not provided on the website. |
1. Prisma Cloud
Reputable and Reliable cloud-native application security capabilities

Overview
Prisma Cloud leverages the unified method of CNAPP technology from Palo Alto Networks. Accelerates the creation of secure cloud-native apps by enabling seamless collaboration between security and DevOps teams. With the improved and extensive protection features of Prisma Cloud CNAPP, you can protect your serverless and containerized apps. Full security, compliance monitoring, automated threat detection, and more. Pricing starts from $9,000 per year for 100 Business Edition credits. For more information, consult the pricing guide or the AWS marketplace.
Features
- From code to the cloud, guaranteed full-stack safety
- Risk management for identity and access
- Threat identification and investigation are automatic
- Detection and prevention of network anomalies
- Governance, compliance, and visibility
- Security for hosts, containers, serverless, and web apps/APIs
Pros
- No blind spots in vulnerability management and controls
- Built-in compliance monitoring and reporting
- Automated threat intelligence and anomaly detection
- Integrates into CI/CD processes and developer tools
Cons
- Requires AWS support for data classification and governance
- A little more setting and knowledge could be needed for some sophisticated functions
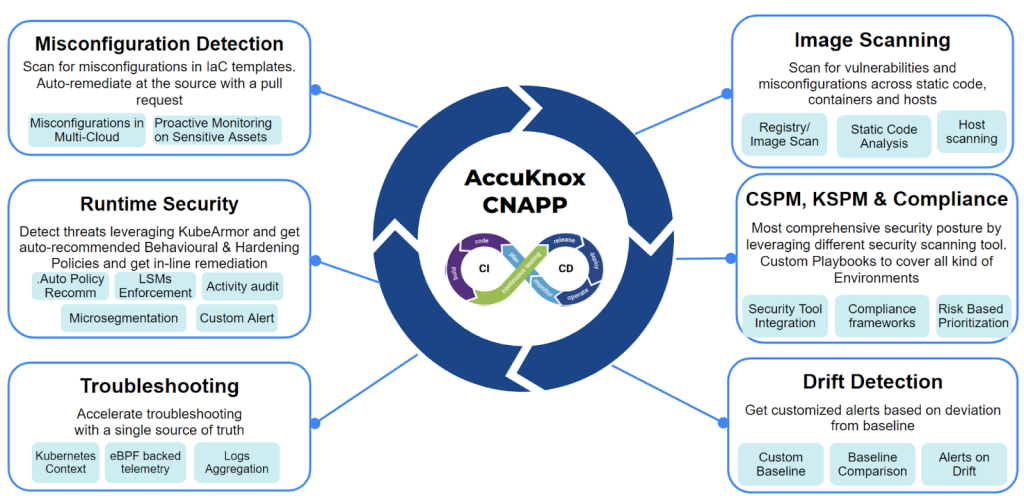
2. AccuKnox
Best overall protection with Agent and Agentless Models. Support for VMs, Bare Metals, 5G, and IoT/Edge tooling in addition to CSPM, KSPM, and CWPP.

AccuKnox goes above and beyond industry standards to safeguard your infrastructure and applications. It maintains security across the software development lifecycle by using a DevSecOps technique and an open-source policy. 5G, Kubernetes, bare metals, VMs, IoT Edge, and both public and private clouds are all supported by CNAPP.
AccuKnox provides an all-encompassing Cloud Workload Protection Platform (CWPP) and Cloud Security Posture Management (CSPM) solution.
| CSPM | CWPP |
| 1. Static Application Security Testing (SAST)2. Software Composition Analysis (SCA) 3. Network security4. API Security5. Host Security6. Container Security7. Kubernetes Orchestration Security 8. Continuous Compliance 9. Baselines & Reporting | 1. Runtime Kubernetes Security 2. Runtime On-Prem Security 3. Zero Trust workload hardening policies 4. Inline Remediation5. Automatically Discovered Policies 6. SIEM, Notifications, Ticketing tools integrations 7. Network micro-segmentation |
The CNAPP Starter Package grants you access to 100 units for a monthly fee of $2,500, allowing you to maximize the potential. With a monthly unit price of $25 per asset, it is scalable and affordable for organizations of all sizes.
Features
- Counteracts zero-day assaults with deep observability, inline remediation, and agentless CSPM
- Driven by the Open Source Cloud Native Computing Foundation’s KubeArmor project
- Zero-trust micro-segmentation, application firewalling, and kernel hardening
- Establishment of zero-trust policies, detection of drift, and continual compliance monitoring
- Supports compliance standards (CIS, NIST, PCI DSS, GDPR, HIPAA, and SOC2)
- SOAR integration for security orchestration, automation, and response
Pros
- Future-proof, includes support for IoT, Edge, and 5G
- Created by DevSecOps specialists who are committed to client satisfaction
- Continuous research and development partnership, as well as many patents
- Good support for public, multi-cloud, and private cloud systems
- Safe security for both traditional (Virtual Machine) and modern (Kubernetes) workloads
Cons
- Relatively new product, not as established compared to most solutions in the CNAPP market.
- Features like 5G, and IoT/Edge Technologies are still in the roadmap/early stage.
3. Check Point CloudGuard
Shines in K8s and Runtime Mitigation

Check Point CloudGuard’s unique proposition is the combination of CWPP and CSPM. It is an ideal choice for enterprises seeking improved container security and runtime protection. With a common dashboard, policy rule set, and support for both agent and agentless monitoring, Check Point CloudGuard has advanced security features to safeguard your cloud-native applications.
While Check Point has not disclosed specific pricing details, you can contact their sales team for custom quotes. AWS Marketplace provides some pricing information, starting at $625 per month for 25 assets.
Features
- Defends against threats on all significant cloud computing platforms, including Amazon, Azure, Google Cloud, Cisco ACI, VMware NSX, Ali, and Oracle.
- Unified cloud traffic, security alerts, and asset visualization with auto-remediation capabilities.
- Gives DevOps teams the tools they need to evaluate their security posture, get help configuring things, get alerts, and manage governance during CI/CD.
- Controls are integrated into CI/CD tools like CloudFormation and Terraform, allowing for pre-deployment security assessments and scaling over a large number of cloud assets.
- Specifies application behavior and profiles it, establishing zero trust boundaries across cloud workloads like serverless architectures and containers.
- Delivers effective online and API security with multi-layer protection tailored for the cloud-native environment, runtime code analysis, and security hardening.
- Auto-remediation capabilities, updates security and compliance industry standards, and guards against misconfigurations.
- Adheres to industry and regulatory standards such as PCI-DSS, NIST CSF/800-53, CIS Benchmarks, and HIPAA. High Fidelity Posture Management (HFPM) is also made available to Situational cloud infrastructure across 300+ native cloud services.
Pros
- Built-in runtime safety and container security
- Appropriate for large companies using the SaaS delivery model
- Integration for improved security with CSPM and CWPP
- Proactive security measures and threat intelligence
- Governance and compliance elements to guarantee compliance with regulations
- Simplified DevOps techniques for secure development
Cons
- Contacting Check Point Sales may be necessary to get more precise price information
- More configuration and setup may be needed for advanced features and add-ons, driving up prices
4. CrowdStrike Falcon Cloud Security
Suitable for threat protection in cloud infrastructure.

Now specializing in threat hunting, CrowdStrike Falcon Cloud Security Platform speeds up responses and improves security in cloud environments. You get a complete solution that combines container security, Cloud Workload Protection (CWP), Cloud Identity and Entitlement Management (CIEM), and Cloud Security Posture Management (CSPM) into one CNAPP offering.
They put a lot of effort into making “1-Click XDR” a snap for safeguarding cloud workloads. With one click, this capability deploys the CrowdStrike Falcon agent on unsecured cloud workloads. CrowdStrike provides cloud application security without the need for an agent for those who prefer agentless choices. With full visibility and repair capabilities both before and during runtime, agent-based technology serves well.
With the entry-level Falcon Go bundle, CrowdStrike Falcon charges a reasonable starting price of $300 annually. AWS is a good resource for more information about prices.
Features
- Streamlined compliance enforcement
- Delivers multi-cloud visibility, continuous monitoring, and threat detection
- CI/CD support by detecting and safeguarding all workloads.
- Strong privilege access control, identity-based security, and policy enforcement.
- Before deployment, perform one-click remediation testing to guarantee a secure application environment.
- Supports hosts, Kubernetes, and containers in environments on Amazon, Azure, and Google Cloud.
- Vulnerability discovery in any cloud set, from development to production.
Pros
- 100% coverage for cloud workload protection and cloud security posture management (CSPM) integration
- Low CPU consumption with little effect on system performance.
- Get a complete and accurate picture of the cloud threat landscape.
- Workloads in the cloud are visible and monitored in real time.
- Machine learning and advanced behavioral analytics to identify and defend against threats.
- Non-stop checks for odd activity and issues alerts.
Cons
- User account management for detecting insider threats might be enhanced, according to certain users.
- Some advanced features could call for more configuration and cost more money.
5. Wiz
Best for an easy-to-use UI and Low Maintenance

Wiz offers a single solution for all cloud security requirements with its centralized model. Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), and other capabilities are tied together. Wiz ensures a solid security posture by making it easier to identify and correct misconfigurations in your cloud environment. Through the use of a graph-based database, it provides a thorough view across various layers of a cloud environment. This assists in the detection of breach paths and related risks. This intelligent automation and seamless interaction is reported to empower SOCs.
On their website, Wiz does not provide price information. To learn more about their plans and to request quotes, get in touch with Wiz Sales. Wiz’s price list is part of what is available on AWS.
Features
- Quick data classification and scanning for databases, data volumes, and buckets
- constant detection of exposed essential data.
- The ability to detect data flow and lineage using schema matching
- Automatic compliance evaluations to confirm the ongoing application of security regulations
- agentless scanning that is easily put into practice.
Pros
- Architecture that is agentless and relies on graphs.
- By using Wiz deployment, your whole cloud environment—including VMs, PaaS, buckets, serverless operations, containers, storage volumes, and DBs—is scanned using only one cloud role.
- Data normalization across clouds, architectures, pipelines, and runtimes is made possible by a common platform, data layer, and policy framework.
- Prioritizes tasks through a solitary risk queue, streamlining the risk reduction workflow.
Cons
- Pricing might be more expensive and unpredictable. No information is available publicly.
- Contacting the customer success team has reportedly proven difficult for certain consumers.
- There is a free demo accessible even if the website does not mention a trial version.
6. DeepFence ThreatMapper
Cloud-based security observation platform for scanning, mapping, and ranking vulnerabilities.

ThreatMapper is a free two-week trial of an open-source security observation platform. It satisfies the crucial need of product development organizations to scan and rank security vulnerabilities within the software development lifecycle (SDLC) phase. Thereby, get decreasing future threats and hazards connected with the code. The platform supports multi-cloud and multi-modality applications, as well as real-time threat detection and visualization in production.
Pricing for ThreatMapper is not available on their website. Interested users can take advantage of a two-week trial, and to learn more about pricing, they need to contact the vendor’s support team.
Features
- Mapping the attack surface of applications to find potential vulnerabilities
- Using ThreatGraph, prioritize vulnerabilities for better remediation planning.
- Scalable cloud protection for VMs, containers, Kubernetes, serverless, and more
- Contextualized warnings in real time to enable visibility into security concerns.
- Prioritize crucial cloud security warnings based on exploitability in an efficient manner.
- Supports VMs, containers, Kubernetes, serverless, and other workload types.
- Monitoring features and activity notifications keep people informed.
Pros
- Unrivaled dependability in vulnerability detection, mapping, and rating
- Real-time threat and vulnerability detection across multi-cloud deployments
- Works across several cloud platforms and workload types.
- Contextualized alarms for security observability and effective action
- Allows for real-time visibility into production apps.
Cons
- The threat and vulnerability list for popular CMS platforms such as WordPress, Drupal, and Joomla needs to be expanded.
- Setting up the tool is a bit complex and needs the services of a specialist developer.
- Non-tech business owners experience the learning curve difficult.
- The user interface can be more engaging and user-friendly.
7. Tenable Nessus

Vulnerability assessment with a user-friendly interface, customizable reporting, and automated scans
Tenable Nessus is built by security professionals to meet their demands. It does point-in-time assessments to discover and correct vulnerabilities. Eg. software defects, missing patches, malware, and misconfigurations. Nessus facilitates vulnerability evaluation, prioritization, and remediation using pre-built rules, customized reporting, and real-time updates. Nessus’ Pro and Expert versions have several cost tiers ranging from $3,390 to $5,390 (1-year licenses). Advanced Support services are offered at a greater cost.
Features
- Excellent detection rate, automated scanning, and few false positives
- Compliance testing, perimeter scanning, and configuration monitoring are all performed on the network.
- Static code analysis and black-box testing
- Risk assessment services include vulnerability information and scanning.
- Reporting, asset identification, a single dashboard, and observability (administrative functions)
- Risk prioritization for successful risk mitigation
- Pros
- Simple interface for rapid vulnerability and network scanning Security scans, network scanning, and vulnerability assessments are all possible.
- Capabilities for Automation: Enables automated scanning and reporting chores for increased productivity.
- Appropriate for Sensitive Data. Helpful to businesses such as healthcare, banking, and government.
Cons
- Expensive due to its extensive functionality and support requirements.
- To make optimum utilization of the features, some training or knowledge is required.
- Scans might take a long time, reducing efficiency.
- The decision to use Nessus is influenced by unique software needs.
8. Lacework
Automated cloud security with deep observability, threat detection, and flexible deployment options

Lacework’s cloud security platform makes use of the Polygraph Data Platform to deliver automated security for Amazon, Azure, Google Cloud Platform, and Kubernetes environments. It identifies aberrant behavior and offers continuous visibility. Primary services include – discovering vulnerabilities, misconfigurations, and malicious actions by utilizing machine learning and behavioral analytics.
Lacework has a unique licensing structure that defines a “resource” as 200 resources per “Lacework unit.” The licensing price is a one-time fee with no other fees, and discounts may be offered.
Features
- Dashboards, reports, and auditing gives a full view of the situation and governance.
- Recognises and responds to typical security events aimed at cloud servers and containers.
- For optimal security, it supports both agent and agentless solutions.
- Identify and correct non-compliant IaaS account setups.
- Security Insights provides early risk mitigation alerts to DevOps and security teams, increasing productivity.
- Monitors and mitigates hazards to meet regulatory standards.
Pros
- A detailed view into cloud accounts, workloads, and microservices
- Rapid threat identification and response to security incidents affecting cloud infrastructure
- For simplicity of implementation, choose between agent and agentless solutions.
- Better security practices for rolled out security patches.
- Contextual notifications reduce data silos and expensive investigations.
Cons
- In particular contexts, the lack of FedRAMP moderate authorization limits usage.
- Connectivity with third-party systems such as Slack and Datadog and the alert setup is tough.
9. Sysdig
CDR and CNAPP solutions with 360-degree visibility, real-time incident response, and threat detection

Sysdig integrates cloud detection and response (CDR) and cloud-native application protection platforms (CNAPP). Based on the open-source Falco. With agent and agentless deployment options, it identifies threats across clouds, workloads, identities, and third-party apps. You get a full range of features such as identity threat detection, incident response, software supply chain detection, and live mapping.
Sysdig has custom quotations and price information is accessible on AWS Marketplace beginning at $720/year for the regular Sysdig Secure plan. Extra consumption is $0.125.unit.
Features
- Detects cloud threats without installing Falco on infrastructure.
- Protects against identity attacks by connecting Okta events with cloud and container activity.
- Extends threat detection throughout the software supply chain, notifying developers and security teams.
- Prevents unauthorized executables being executed that do not originate from the original container.
- Get real-time issue response as well as live mapping for dynamic infrastructure views.
- Shows attack vectors from user to process to remove threats.
- MITRE framework mapping for a unified view of security threats across clouds, containers, Kubernetes, and hosts.
Pros
- Effective runtime assault prevention (drift control capability)
- Kubernetes Live enables quicker issue resolution.
- Combines agent-based and Falco-based techniques.
- Detects identity threats using Sysdig Okta detections.
- Remedies Software Supply Chain Issues and Identifies problems using Sysdig GitHub detection.
Cons
- Pricing information is only provided on request.
- For effective deployment, further training may be necessary.
- No substantial unique offering, it is decent but does not provide any signature features.
10. Virsec
Continuous cyber threat protection with a zero trust architectural approach

Virsec is an enterprise cybersecurity solution based on the Virsec Security Platform (VSP). It uses compensating security controls to enforce runtime execution of authorized scripts, libraries, and dependencies. Their focus is on hardening Windows and Linux Host OS servers, applications, and web workloads in real time. Pricing is not publicly disclosed, so interested users must contact them through their “Talk Now” page.
Features
- Virsec guards against advanced cyber threats in real time, countering zero-day exploits with minimal dwell time.
- It adheres to the concepts of zero-trust architecture and has host protection for web applications in public cloud settings.
- The Virsec deployment procedure is simple, with a rapid time to value and excellent implementation support.
- Continuous protection is ensured by automated security mechanisms, and a deterministic threat detection system detects threats across different workload tiers.
Pros
- Customers like how simple the deployment process is.
- Provides strong protection for Windows server settings.
- Competitive protection using automated security methods
- The Virsec support crew is quick to respond and helpful.
- Responds to viral attacks, ensuring effective threat mitigation.
Cons
- Users reported installation difficulty and required engineers’ help.
- Customers suggest vendors offer certification programs for technical teams since technical documentation is lacking and the learning curve is higher.
- Initial deployment required resources, but the newer version needed one VM.
11. SUSE NeuVector
Container security solution for the entire lifecycle, including continuous protection, compliance enforcement, and visibility.

SUSE NeuVector delivers ongoing container security and compliance technology that enables full container infrastructure security while preserving business velocity. They do not publish prices, but interested consumers can request a security demonstration.
Features
- Deep Packet Inspection (DPI) aids in the detection of attacks, the detection of sensitive data, and the verification of application access, thereby minimizing the attack surface.
- Real-time protection defends apps against internal threats such as DDoS and DNS.
- Packet Capture for Investigation makes threat investigation easier.
- With K8s custom resource definitions, automated security policies protect application workloads.
- Compliance assures the prevention and enforcement of PHI and PII exposure, as well as compliance with standards such as PCI-DSS, GDPR, and HIPAA.
Pros
- The vendor offers excellent value, performance, and cost.
- Customers have reported easy deployment, a good experience, and deep visibility.
- Industry reviews praise the tool’s risk capabilities, deployment simplicity, and useful features.
- Tested runtime container security and extensive network visibility.
Cons
- Users propose that monitoring and reporting features, integration with other security solutions, and cost comparison be improved.
- Training is needed to master vulnerability scans and security features.
- Overlooked documentation and visibility into other DevSecOps pipeline parts.
12. Aarali Networks
Cloud-native risk assessment, threat neutralization, and regulatory compliance implementation

Araali Networks offers an all-encompassing solution for lean security teams to find and prioritize vulnerabilities in data, services, and backdoors. Their cloud-native controls, or an EBPF firewall, have an automated CVE patching capability. Araali provides a freemium plan with the possibility of a demo to cloud-native startups, mid-market corporations, and government agencies.
Features
- Shields 2FA for Crown Jewel apps
- One-click enforcement, reduced overhead, high-risk apps, and zero-day vulnerability protection in the future
- Supports custom, third-party, and open-source applications without requiring code recompilation
- NIST-compliant.
- eBPF-based implementation makes regulatory compliance affordable by doing away with pricey signature matching.
Pros
- Versatile Policy Engine that detects irregularities in all data and network planes.
- Rapid response to critical zero-day threats.
- Responsive and supportive startup team.
- Novel Solution
Cons
- A relatively unknown security solution in the industry.
- As it is an early-stage startup, documentation may need to be improved.
- Few Testimonials. Not enough online presence. May not be fully tested or suitable for enterprise applications.
13. Orca Security
SideScanning powered agentless cloud security for multi-cloud visibility, vulnerability management, and compliance assurance.

Orca Security provides a revolutionary agentless cloud security platform that includes SideScanning technology. It simplifies security, minimizes costs, and allows agent-free monitoring of serverless apps and other cloud assets. Orca enhances security by identifying and prioritizing high-risk attacks and ensuring coverage across various cloud accounts.
Their official site does not mention pricing information. You might need to contact Orca Security for a detailed pricing plan.
Features
- SideScanning collects external data in workloads without using agents.
- Non-Intrusive Approach to monitoring serverless apps and decreasing attack surfaces.
- One-Size-Fits-All Solution. No confusion and redundancy.
- Detects system flaws, lateral movement dangers, malware, and other threats.
- Protects serverless, containers, VPCs, keys, storage buckets, and other cloud assets.
- Get visibility, identify threats, and control vulnerabilities.
- Automates security and generates notifications for proactive threat response.
Pros
- It presents a visual risk context map by combining workload intelligence and cloud settings.
- Visibility and coverage are achieved without affecting users or workloads.
- SideScanning shows a unified picture of the whole cloud network.
- Assists in demonstrating regulatory compliance as well as doing security due diligence.
- Managing and Securing Several Cloud Environments
Cons
- Limited Automated Remediation. Additional auto-remediation choices would be good.
- Setup and Hardening are difficult to setup. Guidance required.
- Increased Emphasis on General Compliance. Increasing attention to include general compliance requirements
- Simplifying the interface to make it easier to use, particularly for non-technical users
Conclusion
The ultimate CNAPP vendors, including AccuKnox, Wiz, CrowdStrike Falcon Cloud Security, Check Point CloudGuard, and Prisma Cloud, are champions in cloud security and emerging technologies. These unified solutions combat cyber threats and protect your cloud kingdom. But, these vendors are not for the big leagues.
AccuKnox and Lacework are beacons of hope for small to medium-sized businesses. They prove that even underdogs can triumph in cloud security. With these CNAPP platforms, your organization can soar to new heights. Your security engineers will navigate operational complexities and replace cumbersome apps in a simplified way.
Some CNAPP vendors offer free trials, allowing you to try them out and see how they fit your enterprise. Remember, the protection of cloud-native applications is crucial, and CNAPPs unlock simplicity and security. Yet, no single solution fits all, and each organization has its own unique requirements and battles to face.
When choosing your CNAPP, delve deep into the capabilities you need and find the vendor whose strengths align with your vision and ambitions.